Understanding the Digital Gatekeeper: Legal Perspectives on Website Verification
In today’s interconnected world, when you visit a website, you may sometimes be greeted by a message asking you to verify that you are a human. This seemingly simple process is actually a gateway to a complex system of online security and legal oversight. The message—“azcapitoltimes.com Verifying you are human. This may take a few seconds. azcapitoltimes.com needs to review the security of your connection before proceeding. Verification successful Waiting for azcapitoltimes.com to respond… Ray ID: 94469392f9092a3f Performance & security by Cloudflare”—is not merely a technical procedure, but a small window into how modern websites manage user authentication and protect data.
At first glance, this brief notice could be considered just another hurdle in our daily online activities. However, a closer look reveals many tricky parts that shine a light on the legal and operational challenges that come with securing digital interactions. In this article, we will poke around and take a closer look at the legal and technological elements behind such verification processes, diving into the tangled issues of cybersecurity, privacy, and the legal side of technology law.
Cloudflare’s Role in Protecting Web Security: An In-Depth Look
Cloudflare is a key player in the world of web security, and the apparent verification message is a testament to its presence. As a global service provider, Cloudflare examines every request coming to a website, ensuring that each one is genuine and not part of any malicious activity. This security check is essential not only for the protection of the site itself, but also for the protection of the visitors.
When users see this message, they may wonder why their connection must be reviewed and what legal measures underpin such processes. Here, we can break down the main issues that define these technologies and their legal implications:
- The Legal Justification: Digital verification falls under several legal frameworks, including data protection laws and cybersecurity regulations enforced by the relevant authorities.
- Protection of Personal Data: By making sure that only human users access sensitive parts of a website, these systems help to minimize the risk of data breaches and unauthorized data captures.
- Prevention of Fraud: The control mechanism is also a deterrent against online scams and fraudulent activities, protecting both website owners and users.
This approach, however, is not without its nerve-racking aspects. Some users express concerns about privacy and the potential misuse of data. Against this backdrop, critical legal discussions have arisen concerning data rights, consent, and the responsibilities of digital gatekeepers.
Digital Verification and the Law: Key Considerations for Privacy and Security
The evolving landscape of digital legal standards means that verification systems must balance thorough security checks with respect for individual privacy rights. The process of verifying that you are human is intertwined with several legal considerations that continue to prompt debate among lawmakers and technology experts.
Balancing Security Measures with Privacy Rights
One of the key twisted issues is finding a balance between robust security measures and the protection of user privacy. On one side, website owners and service providers must defend against cyber threats, while on the other, users demand transparency and control over their personal data. The following points illustrate the legal tightrope that defines modern verification systems:
- Consent and Disclosure: Under many data protection laws, such as the General Data Protection Regulation (GDPR) in Europe, users must be informed about how their data is used during the verification processes. This includes how data is analyzed to confirm whether a visitor is human.
- Data Minimization: The principles of data minimization require that only the essential data needed to perform the check is collected and stored, reducing the risk of any breach of privacy.
- Jurisdictional Differences: Privacy laws differ significantly around the globe, which means companies like Cloudflare that operate internationally must make sure their processes meet a wide range of legal standards.
These points underscore the need for ongoing legal vigilance. Online security is a persistent challenge, loaded with issues that require continual reflection and regulatory updates as technology advances.
Technical Validation and Its Legal Backbone
At the core of the verification process is a technology designed to differentiate between human users and automated bots. This technological mechanism, while seemingly straightforward, is built on a foundation of complex legal principles related to intellectual property, cybersecurity, and even contract law. Understanding this technical validation helps illustrate why the legal system must keep pace with rapid technological evolution.
How Digital Tools Shield Websites Legally
Legal protection of websites involves a combination of technical smartness and legal safeguards. For Cloudflare and similar security services, the system is more than just a series of algorithms—it is a legally driven tool that steps in to protect both the service provider and the end-user. Here are some vital aspects:
- Intellectual Property Rights: The software and algorithms used in verification systems are often protected by copyright and patent laws. This legal safeguard helps to ensure that the innovative processes behind digital security are not easily replicated by malicious entities.
- Security Protocols and Breach Response: In addition to preventive measures, these systems are programmed to alert administrators of any unusual activity that could signify a breach, thereby activating legal protocols designed to mitigate damages.
- Contractual Agreements: When websites employ services like Cloudflare, they enter into contracts that outline the respective responsibilities and liabilities of each party. These agreements are crucial for establishing clear legal boundaries and expectations.
This combination of legal and technical measures is the bedrock upon which the modern internet is built. By ensuring that technology aligns with legal standards, companies can better protect users while also minimizing legal risks that might otherwise derail operations.
Interpretation of the Verification Process in Today’s Legal Climate
For many users, the verification process can feel like an unneeded hurdle. However, observing the law from a broader perspective reveals a more nuanced understanding of why these steps are implemented and what they mean for our daily internet usage.
Legal Implications of User Authentication
User authentication is not simply about keeping bots at bay; it is a legally important procedure meant to protect online interactions. The verification procedure reinforces several legal principles:
- Protection of Digital Identity: Authenticating that a user is human helps preserve the integrity of digital identities, reducing the risk of fraudulent activities.
- Regulatory Compliance: Many jurisdictions impose strict requirements on digital businesses related to consumer protection. Verification processes help companies achieve compliance with such laws by ensuring that user interactions are genuine.
- Dispute Resolution: In cases where disputes arise over unauthorized access or data breaches, a solid authentication system backed by legal protocols can provide evidence supporting the actions taken by website administrators.
These considerations form the basis for legal debates and policy recommendations that are crucial in an era where digital interactions are the norm. The rules governing these interactions are continually refined as both technology and legal frameworks evolve, leading us to ask: How can we best protect the digital landscape while respecting individual rights?
Examining the Impact of Verification Systems on Freedom of Information
Verification systems, though primarily designed for security, also carry implications for freedom of information and access to online content. As these systems become more common, they raise questions about whether they inadvertently restrict access or inhibit free expression.
Balancing Access with Security
Internet freedom is a cherished idea, yet ensuring that only genuine users access content is a necessary restriction in an age where cyber threats are rampant. Here are some key points that capture this balance:
- Access Limitations: While verification processes delay access slightly, they are a countermeasure against the misuse of digital platforms. Importantly, these measures are designed not to block legitimate users but only to filter out dangerous activity.
- Improved User Trust: Knowing that websites are protected against bot-induced spam and malware helps to build trust among users. This trust is crucial for upholding the principle of open access in the digital age.
- Legal Safeguards: The implementation of these security measures is governed by legal frameworks that ensure the rights of individuals are upheld. Even though there might be off-putting delays, the long-term benefits of improved security far outweigh the temporary inconvenience.
The trade-off here is clear: a slightly slower access process is a small concession for enhanced security. However, these decisions are never taken lightly, with policymakers and industry leaders continually discussing how best to respect both freedom of information and the necessity of robust security measures.
The Role of Verification Systems in Modern Litigation and Policy Enforcement
Digital verification processes have implications that extend well beyond the initial user experience. They play a significant role in modern litigation and policy enforcement, especially as disputes over digital rights and responsibilities become more prevalent in courts worldwide.
Mitigating Legal Risks for Online Platforms
The adoption of advanced verification steps is a proactive measure to reduce legal exposure. Here are some ways that these systems help manage legal risks:
- Evidence Collection: In the event of a security breach or a data theft case, the records of digital verification can serve as evidence showing due diligence on the part of the website operators.
- Compliance with Regulatory Standards: By implementing verification systems, companies demonstrate their commitment to meeting regulations set forth by authorities, thereby reducing the likelihood of fines and sanctions.
- Risk Mitigation Strategies: Such systems are designed to quickly identify abnormal behaviors, allowing companies to intervene before a small glitch turns into a larger legal issue.
The legal benefits of these verification processes are substantial. They not only help protect websites from cybercrimes but also serve as a critical line of defense in any subsequent legal disputes. This proactive approach underscores a broader trend: the merging of technology with legal compliance to safeguard digital communication channels.
Sorting Through the Finer Points of Cloudflare’s Security and the Law
Cloudflare’s role in ensuring online security is emblematic of many modern technological solutions that intertwine legal mandates with advanced computer science. While some may see these verification measures as just another hurdle, understanding the legal framework behind them reveals how essential they are to protecting our online lives.
Understanding the Legal Rationale Behind Performance & Security Protocols
At the heart of Cloudflare’s verification lies two central principles: performance and security. This dual purpose is essential in today’s digital age, where fast access is as important as robust protection. Let’s take a closer look at the legal rationale behind these protocols:
| Key Aspect | Description | Legal Implications |
|---|---|---|
| Performance Enhancement | Ensuring that requests are legitimate helps maintain optimal server performance without interruption from spam or automated attacks. | Aids in meeting contractual service level agreements (SLAs) and compliance with consumer protection regulations. |
| Security Checks | Screening for bots prevents malicious software from exploiting vulnerabilities, thus maintaining site integrity. | Minimizes liability for data breaches and supports defense in case of legal challenges. |
| User Verification | Confirming that a visitor is human helps in preserving genuine user interactions. | Helps in establishing a trusted user base and reducing claims of negligence in cybersecurity measures. |
This table illustrates how each technical measure has a corresponding legal safeguard, ensuring that while the website remains secure and efficient, it also complies with various legal regulations that protect both the service provider and its users.
Legal and Ethical Considerations in Automated Verification
Automated verification systems such as those implemented by Cloudflare raise broader ethical and legal issues. While the technology itself is neutral, its application can stir debates about rights, fairness, and transparency.
Ethical Dilemmas and Legal Implications
There are several small distinctions to consider when reviewing the ethical aspects of using automated systems for verifying human users:
- Transparency: Users deserve clear disclosures on how their data is collected and used during the verification process. This is not only a legal requirement in many jurisdictions but also an ethical obligation for companies that value trust.
- Bias in Automation: Some automated systems may inadvertently screen out certain user groups based on flawed criteria. The legal expectation here is to ensure unbiased protocols, a topic that has garnered increasing attention in discussions of digital rights.
- Accountability: When issues arise—such as false positives that restrict access—there must be a clear channel for accountability. Legal frameworks advocate for mechanisms that allow users to seek redress when they are mistakenly caught by these systems.
Addressing these ethical dilemmas is a critical part of modern legal practice and technology policy. Companies must be prepared to adjust their systems to not only meet legal mandates but also to foster a culture of fairness and transparency.
Data Protection and User Consent in the Realm of Digital Verification
Data protection remains one of the super important pillars of online interactions. With verification systems constantly scanning and checking visitor activity, ensuring that users know how their information is used is both a legal and ethical imperative.
How Consent and Data Protection Law Shape Modern Website Security
User consent, a critical aspect of data protection laws across many regions, means that if a website employs automated verification tools, it must notify the visitor and often requires their implicit or explicit agreement. Here are some key points on how these legal frameworks affect digital verification:
- Informed Consent: Regulations such as the GDPR require companies to inform users about the nature of the data being collected and the purpose of its use. This means that behind every verification screen is a legal obligation for clear communication.
- Right to Access: Users often have the right to request information about the data that has been collected about them. This aligns with the principles of transparency that underpin both ethical and legal approaches to data collection.
- Data Security Measures: The very nature of verification systems demands that the data collected is stored and processed securely. Failure to do so can result in severe legal consequences, including fines and sanctions.
By ensuring that data protection principles are integrated into the system, companies uphold both the letter and spirit of the law. This builds confidence among users and sets a precedent for fairness in digital interactions.
Future Directions: Legal Reforms and Technological Advances in Web Verification
As technology continues to evolve, so too will the legal frameworks that govern digital interactions. In the coming years, we can expect to see further refinements in how verification processes are implemented, with discussions focusing on how best to manage the trade-offs between accessibility, security, and privacy.
Emerging Trends and Their Legal Implications
Looking ahead, several important trends are likely to shape the intersection of technology and law in the arena of digital verification:
- Increased Automation with Human Oversight: Future systems may combine the efficiency of automated algorithms with the critical oversight of human review. This hybrid approach promises to reduce errors while maintaining robust legal safeguards.
- Enhanced Data Anonymization: With growing concerns over privacy, the next generation of verification systems may incorporate stronger measures for anonymizing data. Legal standards will continue to push companies toward minimizing the personal data they collect during these checks.
- Cross-Border Regulatory Harmonization: As digital interactions increasingly span multiple jurisdictions, there will be a stronger push for international regulatory frameworks that standardize how verification processes are implemented and enforced.
- User Empowerment Tools: Innovations in digital rights management could give users more power to manage and review the data associated with their online activities. Such tools would support transparency and accountability, two areas of growing legal significance.
These emerging trends reflect an ongoing dialogue between policymakers, technology developers, and legal experts. The objective is clear: to create a digital environment that is both secure and respectful of individual rights.
Conclusion: Weaving Legal Principles into the Fabric of Online Security
In summary, the simple message that appears on your screen—verifying that you are human—opens up a broad discussion on the harmony between technology and law. This process, which may initially seem like a mere technical formality, is actually embedded with a host of legal safeguards designed to protect both the website operator and the visitor. From ensuring data security to balancing privacy rights, every twist and turn in the verification system is a reflection of deep-rooted legal principles.
Cloudflare and similar service providers play an essential role in managing online security, and their systems are laden with measures that not only check if a user is human but also help enforce the law. As we continue to rely on the internet for more aspects of our lives, the legal and technological communities must work together to manage your path through the digital landscape.
Whether it is through ensuring informed consent, protecting data, or mitigating legal risks through robust contractual agreements, modern verification systems offer a glimpse into the future of law and technology. This future is one where legal safeguards are not an afterthought but an integral part of the technological backbone that supports our daily digital interactions.
By taking a closer look at the legal aspects of what might seem like a mundane message on your screen, we can appreciate the substantial effort that goes into maintaining secure and fair online platforms. The fine points of these processes reveal a carefully calibrated balance, one that is constantly being adjusted as new challenges—and new technologies—emerge. In our increasingly digital world, understanding these systems is not just the domain of legal experts and technologists, but a critical insight for every internet user who values privacy, efficiency, and trust in their online interactions.
As we steer through the evolving digital landscape, it remains critical for policymakers, companies, and users alike to figure a path that embraces both progress and protection. Each verification prompt is more than a security check—it is a small, yet powerful symbol of the intricate relationship between modern technology and the law.
Ultimately, this dialogue between our digital experiences and legal frameworks underscores the need for continued vigilance. Whether it’s adjusting newly introduced automated measures or adapting to international regulatory reforms, the future promises further integration of legal standards into the technical systems that underpin our web interactions. This ongoing evolution is a testament to the collective effort to create an online environment where the rights of individuals are respected and protected under the law while harnessing the full potential of technology to benefit society.
In closing, the next time you see that simple message asking you to verify your humanity, take a moment to appreciate the hidden complexities behind it. What appears to be a momentary pause is actually the culmination of tireless work by legal experts, technologists, and policymakers—all dedicated to creating a safe, efficient, and legally compliant space for the vast and ever-growing community of internet users. As we continue to adapt and innovate, these systems will remain a cornerstone of digital trust, ensuring that every online interaction is as secure as it is seamless.
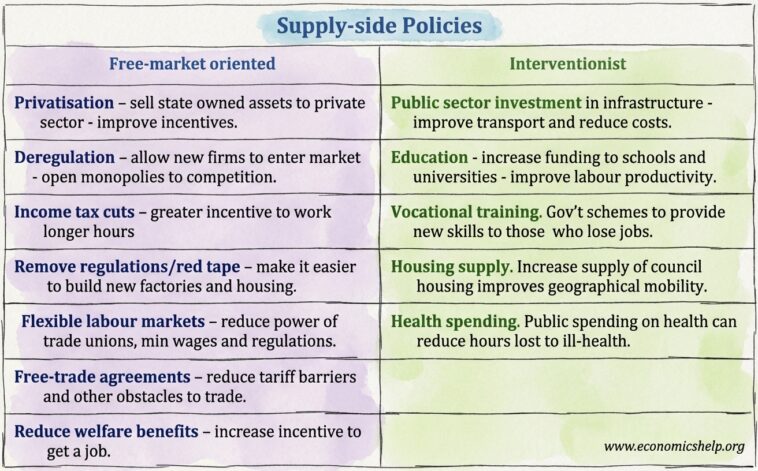
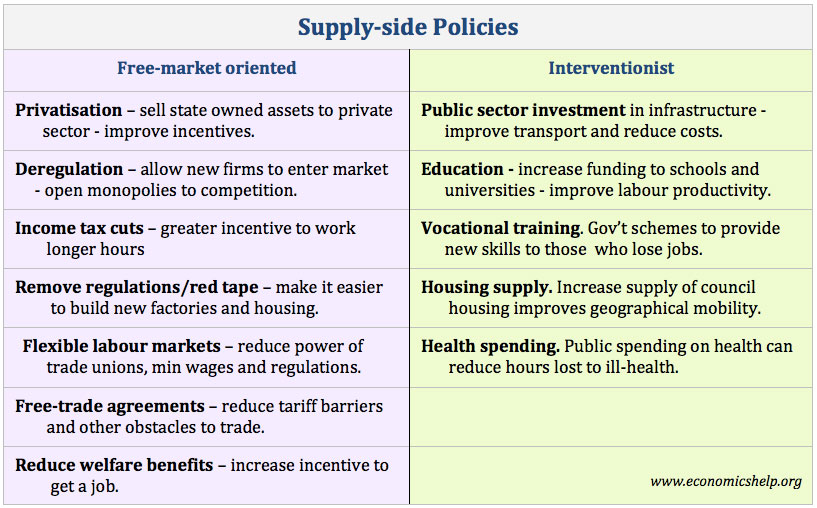
Originally Post From https://azcapitoltimes.com/news/2025/05/22/the-next-frontier-of-education-reform-the-supply-side/
Read more about this topic at
Cloudflare test – Security
Cloudflare Checking if the site connection is secure